
Your Partner in Digital Excellence
Microsoft 365 Defender XDR Deployment
Elevate your organization’s security posture with the Microsoft 365 Defender XDR Deployment. This comprehensive solution provides advanced threat detection and response across all your digital assets. With unified threat protection for endpoints, emails, cloud apps, and identities, you can safeguard your organization against sophisticated cyber threats. Centralized management and AI-driven automation streamline threat response, ensuring quick remediation and minimal business disruption. Embrace a Zero Trust architecture with robust security measures that protect your data and maintain business continuity. Invest in a secure future with Microsoft Security Defender XDR.
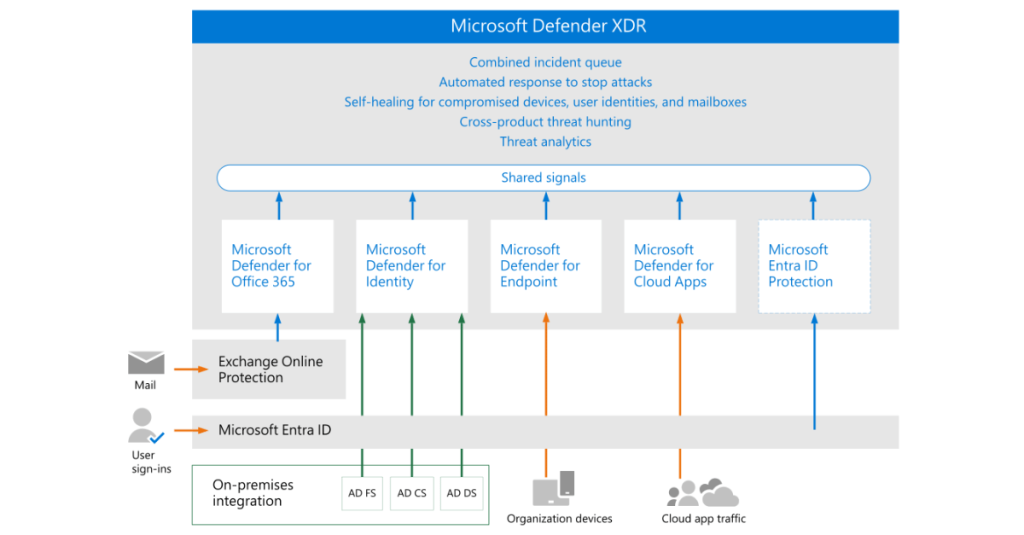
The Microsoft Security Defender XDR provides a comprehensive solution for advanced threat detection and response across your organization. Here are the key features:
- Unified Threat Protection:
- Microsoft Defender for Endpoint: Protects devices against advanced threats, providing post-breach detection, automated investigation, and response.
- Microsoft Defender for Office 365: Safeguards your organization against malicious threats posed by email messages, links (URLs), and collaboration tools.
- Microsoft Defender for Cloud Apps: Enhances visibility, control over data movement, and analytics to identify and combat cyberthreats across all your cloud services.
- Microsoft Defender for Identity: Detects and investigates advanced threats, compromised identities, and malicious insider actions directed at your organization.
- Centralized Management:
- Microsoft 365 Defender: Provides a single pane of glass for managing and responding to threats across all Defender components.
- Automation and AI: Leverages artificial intelligence and automation to automatically stop some types of attacks and remediate affected assets to a safe state.
- Zero Trust Architecture:
- Comprehensive Security: Contributes to a strong Zero Trust architecture by providing threat protection and detection across identities, endpoints, email, and cloud apps.
- Business Continuity: Helps prevent or reduce business damage from a breach, ensuring continuous protection.
This offer is ideal for organizations looking to enhance their security posture with a unified, cloud-based defense suite.
Ready to take the next step? Submit your inquiry today and let us help you achieve your goals. Whether you have questions about our services, need a customized solution, or are ready to get started, our team is here to assist you. Simply fill out our inquiry form, and one of our experts will get back to you promptly. We look forward to partnering with you and providing the exceptional service you deserve. Don’t hesitate—reach out now and let’s begin this journey together.